Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

For critical infrastructure industries such as electricity generation, transportation, oil and gas, utilities, and telecommunications, the main concern is keeping services up and running. Any disruption could result in a loss of vital services. For other critical industries, such as aviation and transport, a loss of service can cause productivity and revenue loss, partial loss of view for human operators, disruption to physical processes and can lead to reputational damage.
Old operational technology (OT) equipment was primarily built to ensure availability rather than to be secure. In general, OT systems have been isolated from IT systems in the past, but as infrastructure companies move to new technologies, there are operational threats to the old systems. It can be a balancing act between changing policy, improving services, and managing the risk of making changes.
Threats often originate from IT networks and get passed on to OT systems. Security teams lack visibility of IT traffic and anomalies, which allow them to protect the OT network. Instead, OT teams need to adopt a reactive approach for detecting these threats so that these vulnerabilities can be mitigated.
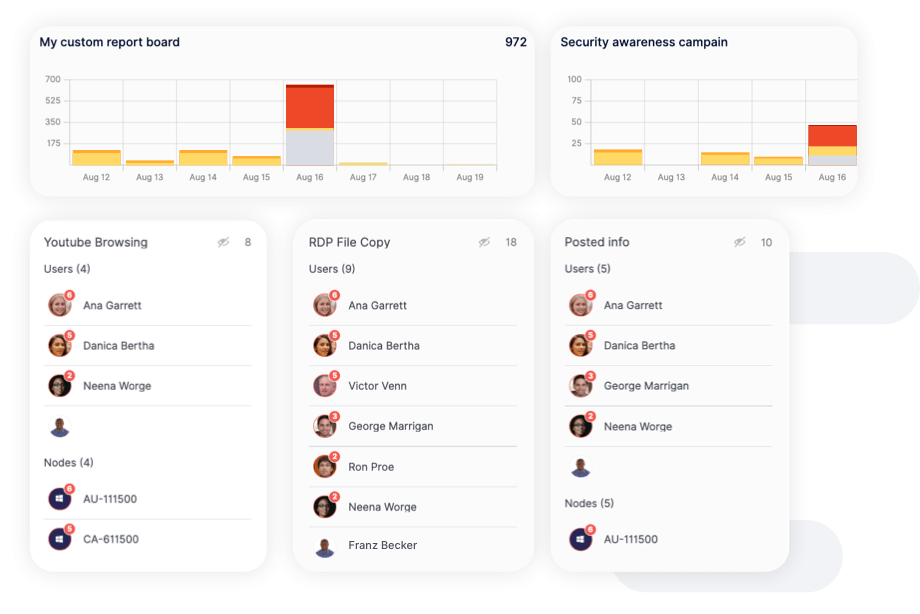
Faced with threats to OT systems that often originate from IT networks, security teams need visibility of IT traffic and anomalies. Choose Reveal to improve supervisory control and data acquisition (SCADA) security as the first and most critical step to gain visibility.
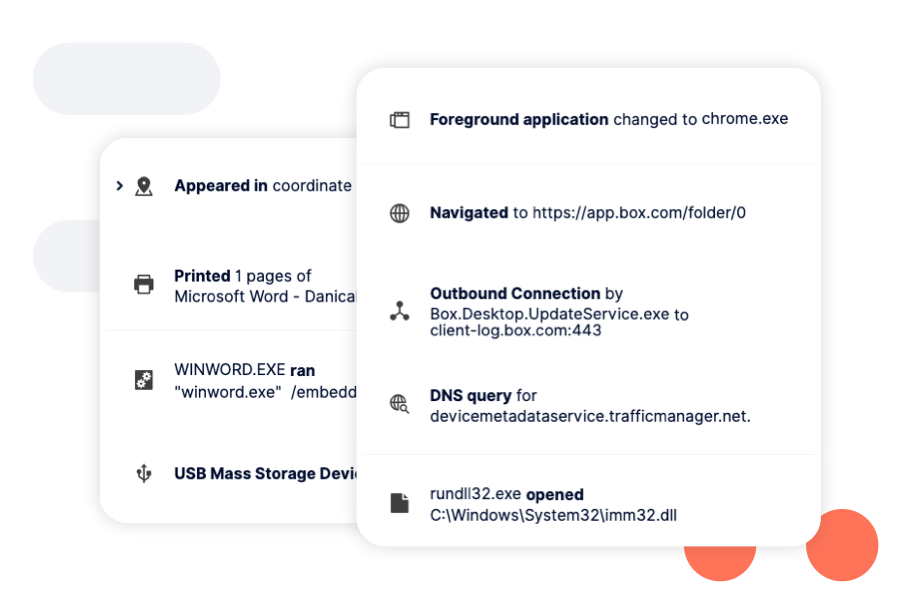
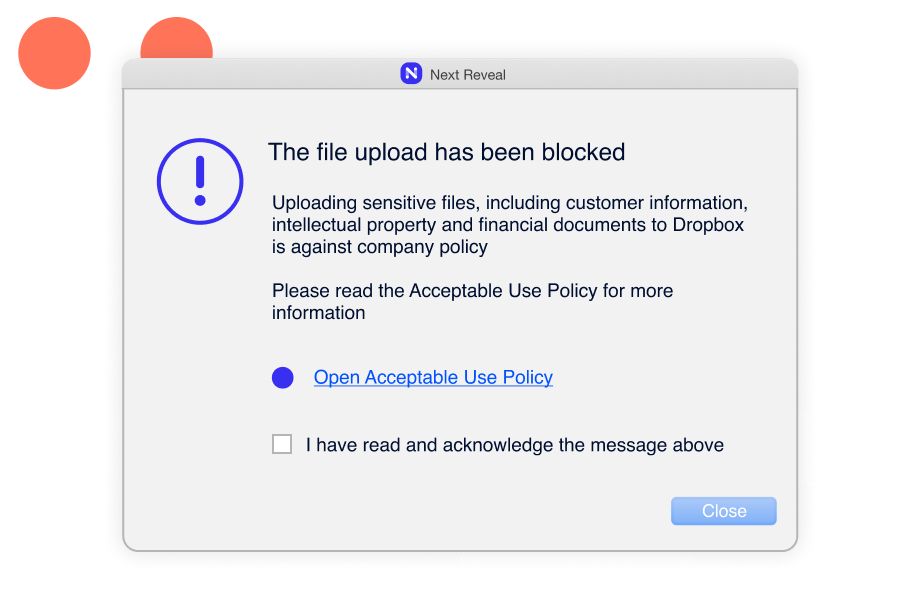
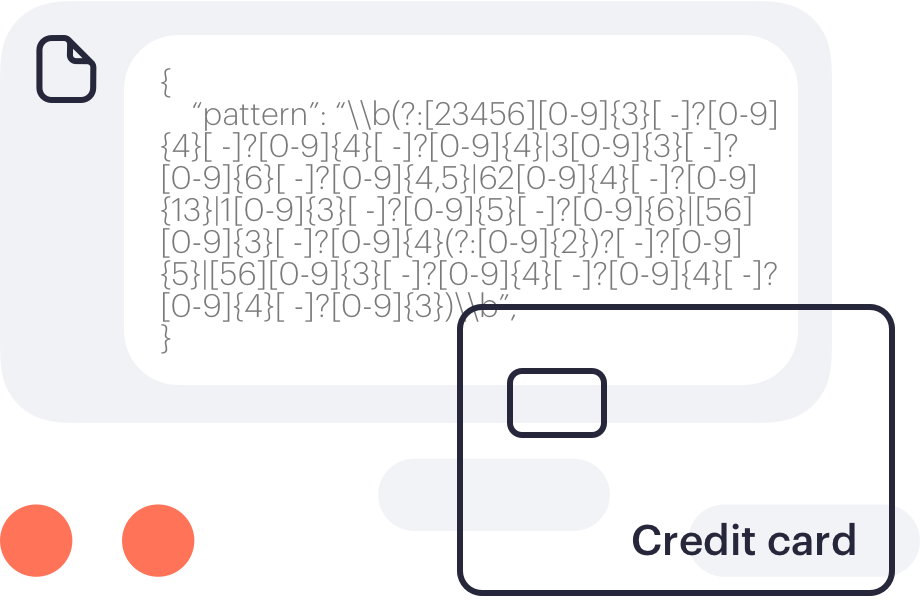

Identify and manage risk and vulnerabilities with the help of Next DLP Cyber Analysts. Experienced cybersecurity specialists with a strong background in security monitoring, CIRT, and incident response; our analysts can create risk assessment reports customized to your organization.