Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
Zero Trust security is an approach to protecting an organization’s IT systems and data assets. The main principle of Zero Trust is to never trust and always verify every interaction with the computing environment. All requests for access to IT resources must be authorized, authenticated, and validated.
Another core principle of Zero Trust is that threats can come from inside or outside the environment’s network perimeter. Therefore, requests from within and outside the network are subjected to the same degree of verification. Entities must be authenticated and authorized for each specific request regardless of where the request originates.
The multi-cloud and hybrid IT environments employed by many organizations introduce additional complexity and risks to a company’s valuable and sensitive information. Extending Zero Trust to the endpoint provides enhanced security by ensuring that no entity can access IT resources without explicit authorization.
Zero Trust is not implemented via a single software solution or technique. Implementing Zero Trust across the complete environment, including endpoints, requires multiple, coordinated activities.
In this article:
Endpoint protection is a crucial component of cybersecurity that helps protect endpoints, such as laptops, desktops, mobile devices, and servers, from cyber threats.
Endpoint protection works by providing several layers of security to prevent, detect, and respond to security incidents. This includes features such as antivirus protection, firewall, intrusion detection system, device control, application control, and more.
These features work together to ensure that endpoints are protected from malware, ransomware, phishing attacks, and other cybersecurity threats.
Zero Trust security has become a hot topic in the cybersecurity world, but does it apply to endpoints? The answer is a resounding yes.
Zero Trust security is a model that assumes the worst when it comes to security threats – that is, no entity, whether inside or outside the network, should be trusted by default. This model requires verification from anyone trying to access the network or resources, regardless of their location or device.
Endpoints, such as laptops, desktops, and mobile devices, are often the entry points for cyber threats into an organization's network. This makes them a crucial aspect of implementing Zero Trust security. By applying Zero Trust principles to endpoints, organizations can better protect themselves from malicious actors attempting to gain unauthorized access.

Zero Trust and endpoint security are two vital components of a comprehensive cybersecurity strategy. While endpoint security focuses on protecting individual devices within a network, Zero Trust takes a more holistic approach by assuming that no device, user, or application should be trusted by default.
Here's how Zero Trust complements endpoint security to create a more secure network environment:

Endpoint security solutions such as antivirus software, firewalls, and intrusion detection systems are essential for protecting individual devices from cyber threats. However, Zero Trust goes a step further by ensuring that even if a device is compromised, access to critical resources is still restricted. By implementing strict access controls and continuous monitoring, Zero Trust helps to prevent lateral movement of threats within the network.
Zero Trust architecture provides organizations with a clear view of their network and the devices connected to it. By continuously monitoring and assessing user and device behavior, Zero Trust can identify and respond to any suspicious activity. This visibility allows organizations to quickly detect and remediate security incidents before they escalate.
Endpoint security focuses primarily on external threats, such as malware and phishing attacks. Zero Trust, on the other hand, also takes into account insider threats – whether intentional or accidental. By implementing least privilege access policies and multi-factor authentication, Zero Trust limits the potential damage that can be caused by insider threats, even on trusted endpoints.

The cybersecurity landscape is constantly evolving, with new threats emerging every day. Zero Trust architecture is designed to be adaptable and scalable, allowing organizations to quickly respond to new challenges and vulnerabilities. By integrating Zero Trust principles with endpoint security solutions, organizations can stay ahead of the curve and protect their networks from emerging threats.
Following are the steps and strategies necessary to extend Zero Trust to the endpoint.
All endpoints with the capability of accessing the IT environment need to be inventoried so they can be managed effectively. This includes mobile devices, laptops, and other connected devices. The inventory must be kept up-to-date to accurately reflect the endpoints that can make requests.
Endpoints should be monitored to detect suspicious behavior or possible threats. This may include installing software tools or incorporating the entity into monitoring solutions. New endpoints need to be added to monitoring processes before allowing them access to the environment.
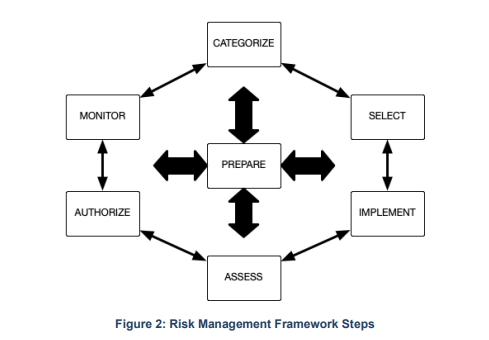
Endpoints should be regularly audited to verify the appropriate security measures are in place. Audits should be accompanied by risk assessments to determine if new mitigation tactics must be employed to address threats. Endpoints that do not meet minimum security standards should not be permitted to access the IT environment.
Strong authentication is mandatory for Zero Trust security. All entities, including users, devices, and applications, need to be authenticated before allowing them to access IT resources. Requests originating from endpoints will typically require multiple types of authentication to ensure the device and user or application are making a legitimate request.
Multi-factor authentication should strongly be considered when authenticating endpoints. The fact that these entities live outside the corporate network increases the likelihood that they can be compromised by threat actors. Requiring a form of authentication in addition to a password helps safeguard the environment.
Endpoints should be secured to protect them from being compromised or misused by threat actors. Endpoint security can take several forms including:

Segmenting the network into specific zones limits the ability of threats to affect large parts of the IT environment. Endpoints should only be able to access segments rated to their function within the infrastructure. Network access controls can be used to control endpoint access to the network.
Sensitive and valuable data resources should always be encrypted at rest and in transit. This protects the information from being accessed by unauthorized entities. While the goal of Zero Trust security is to eliminate unauthorized access, encrypting data provides insurance against data breaches.
Users need to receive training so they understand the organization’s data access policies. Some users may find the constant need to authenticate themselves frustrating, especially if it breaks from previous, less secure access practices. Understanding why this new policy is critical in protecting the IT environment will result in more satisfied employees and fewer accidental violations of data handling policies.
One of the most impactful strategies an organization can take when implementing Zero Trust architecture is to enforce strong access control policies. This is where a data loss prevention platform (DLP) such as the Reveal Platform by Next fits in and supports the Zero Trust approach. DLP is essentially a manifestation of Zero Trust focused on a company’s data resources.
DLP tools enforce a company’s data handling policy. This policy should reflect the principle of least privilege and only provide data access related to an entity’s job functions.
The software will restrict all violations indicating unauthorized data requests. Reveal also provides user training when violations occur to help develop security awareness throughout the organization.
Reveal delivers machine learning at the endpoint with intelligent agents that identify and categorize data at the point of risk. The cloud-native platform uses multiple behavioral analytics algorithms to define typical vs. anomalous behavior, providing data protection without a separate analysis engine.
Learn more about Reveal and schedule a demo to see how this valuable tool can help extend zero security to the endpoint.
It is important to extend Zero Trust to an organization’s endpoints primarily because of the support for cloud environments and a remote workforce. The cloud enables anyone with an internet connection to attempt to access sensitive resources. Securing the network perimeter is no longer sufficient.
Remote workers by definition need to use endpoints to access the corporate network. Zero Trust protects IT resources from being misused by compromised endpoints.
Yes, users are impacted by a Zero Trust architecture. The user experience may be less satisfactory due to the multiple authentication requests necessary when supporting a Zero Trust security approach.
Education can help address this issue by providing employees with an understanding of the benefits of Zero Trust versus the potential extra work involved in performing their jobs.
A data handling policy supports Zero Trust by defining the informational resources that can be accessed by specific groups or individuals in the organization. When a DLP tool queries the data handling policy in response to an access request, it exhibits the characteristics of the Zero Trust approach. Even when a user gains access to data assets, subsequent requests are reevaluated, promoting the Zero Trust mindset.

Blog

Blog

Blog

Resources

Resources

Resources

Resources

