Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
The U.S. National Institute of Standards and Technology (NIST) is responsible for developing standards and best practices promoting cybersecurity for federal agencies, businesses, and the general public.
The NIST Zero Trust Architecture (ZTA) is a security framework specifically developed to address the difficulties of securing complex IT environments with resources located beyond traditional network perimeters.
As such, organizations should strongly consider implementing the framework to strengthen their security posture.
In this article:
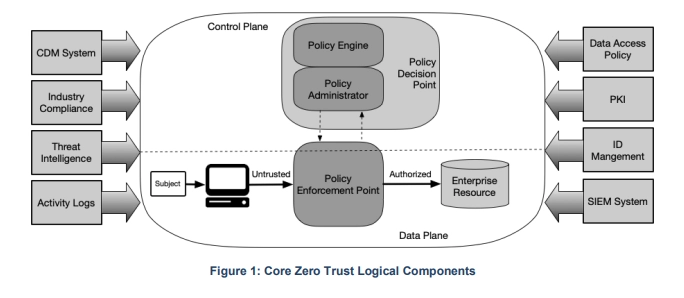
Details of the NIST ZTA can be found in NIST Special Publication 800-207. The document’s purpose is to provide its intended audience of enterprise security architects with an understanding of Zero Trust when used with unclassified civilian IT systems.
It offers its audience a path to migrate and deploy Zero Trust security in an enterprise environment, with additional information focused on implanting Zero Trust in a cloud environment available in NIST Special Publication 800-207A.
The NIST stresses the point that this publication serves as a framework that should be augmented by considerations of a company’s unique business objectives and requirements.
We’re going to discuss the major principles and components of the NIST Zero Trust Architecture and look at how a data loss prevention (DLP) solution can be instrumental in its successful implementation.

The main principle of the NIST ZTA security model states that threats to the IT environment can come from external or internal actors. Trust should never be assumed regarding any entity inside or outside the network.
Threats may already be present within the environment and need to be identified and addressed through a program of continuous verification and authentication.
These following core principles form the foundation of the ZTA model.
NIST SP 800-207 defines the following basic tenets of Zero Trust. Adhering to these tenets is essential for successfully implementing ZTA.
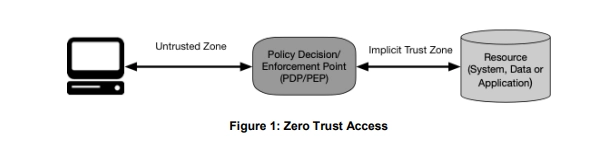
The policy is developed by an organization to address its unique business processes and the level of risk it can tolerate.
Credential and access management using techniques such as multi-factor authentication (MFA) is necessary to protect the environment.
The NIST Special Publication 800-207 delineates three primary models for implementing Zero Trust architecture: Enhanced Identity Governance, Micro-Segmentation, and Software-Defined Perimeters. These models serve as foundational approaches for organizations to adopt Zero Trust principles.
Enhanced Identity Governance focuses on robust authentication and authorization mechanisms, while Micro-Segmentation involves dividing networks into smaller, more manageable segments. Software-Defined Perimeters create dynamic, identity-centric boundaries around resources.
Implementing ZTA requires a comprehensive approach encompassing several key elements. Organizations must effectively manage their assets, thoroughly understand potential risks, and develop robust policies to guide implementation.
Continuous monitoring is crucial to maintain security, while proper configuration of all components ensures the system functions as intended.
When implementing ZTA, it's important to avoid common pitfalls. One such mistake is neglecting compatibility issues between different systems and components, which can lead to integration problems and security gaps.
Another error to avoid is over-reliance on vendor APIs, as this can create vulnerabilities and limit flexibility in the long run. By addressing these aspects and avoiding potential mistakes, organizations can successfully implement a robust ZTA framework that enhances their overall security posture.
Data loss prevention software can be an important component of an organization’s attempts to implement Zero Trust Architecture. Using a DLP solution requires the development of a data handling policy that defines which resources can access and use specific data assets. The DLP platform then automatically enforces the policy, restricting access according to policy definitions.
A DLP solution such as the Reveal Platform by Next protects an organization from external and internal risks to data assets. It contributes to a Zero Trust mindset by enforcing authorization for all attempts at accessing enterprise data.
Schedule a demo to see how Reveal can support your Zero Trust security measures.
A company should adopt the NIST ZTA framework because it streamlines the process of protecting its valuable and sensitive data resources. The framework was developed by experts in the field and incorporates proven best practices that will enhance the security of any IT environment.
Organizations can use the framework as a road map to ZTA implementation, making adjustments to reflect their specific business requirements.
Zero Trust architecture addresses the issue of insider risks by requiring authorization and authentication for every interaction in an IT environment. This approach restricts deliberate or accidental attempts to misuse data resources by employees or contractors already within the infrastructure.
Simply gaining access to a specific system will not permit users to use data resources for which they are not authorized.
The principle of least privilege is important when implementing Zero Trust Architecture because it restricts entities from gaining access to resources that are not necessary to perform their job or a designated task.
This approach meshes nicely with ZTA’s continuous enforcement of authorization and authentication to protect IT resources. Implementing least privilege eliminates the prospect of an entity gaining access to sensitive resources outside of the scope of its role in the enterprise.

Blog

Blog

Blog

Resources

Resources

Resources

Resources

