Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release




A lack of information security professionals is an organization-wide problem.
Insiders may knowingly bypass security–or the identified lack of it. Meanwhile outsiders target organizations they suspect have lower barriers of entry.
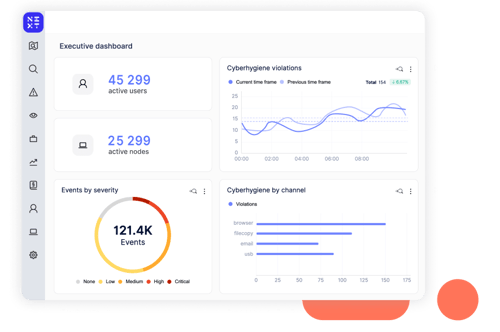
Uncover risks in applications, Wi-Fi network connections, data usage, USB devices, websites visited, and printer activity.
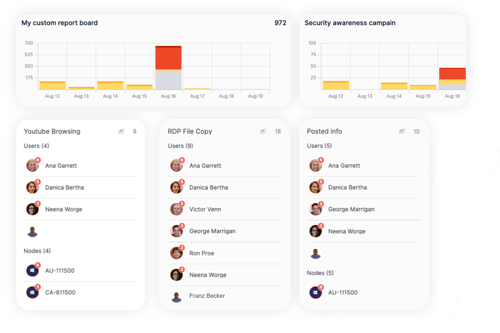
Assess indicators of insider risk based on a single event or a combination of events.
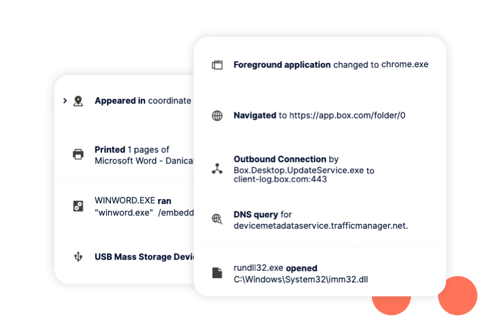
Look closer at applications, servers, web services, or users you need to inspect further based on your specific business needs.

