Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release


Hybrid Cloud-Edge Deployment - Next DLP machine learning operates on both a global scale and localized within the network, so analysis is scalable, reduces false positives, and eliminates latency.
Dual analytics - Machine learning is not infallible, but combined with unconventional dynamic analytics, non-standard attacks can be stopped using both sophisticated artificial intelligence and static rules.
Decisive inference - Next DLP's solution can sequence events, test and weigh attributes simultaneously, and adopts top-level, decision-analysis structures.
Adaptive learning - Continuous recalibration and creative policy suggestions means better machine learning

Get full visibility of your data and endpoints outside of the office. Reveal notifies organizations of unencrypted or unapproved Wi-Fi networks, suspicious login activity, or printing outside office hours, geolocation, and more.
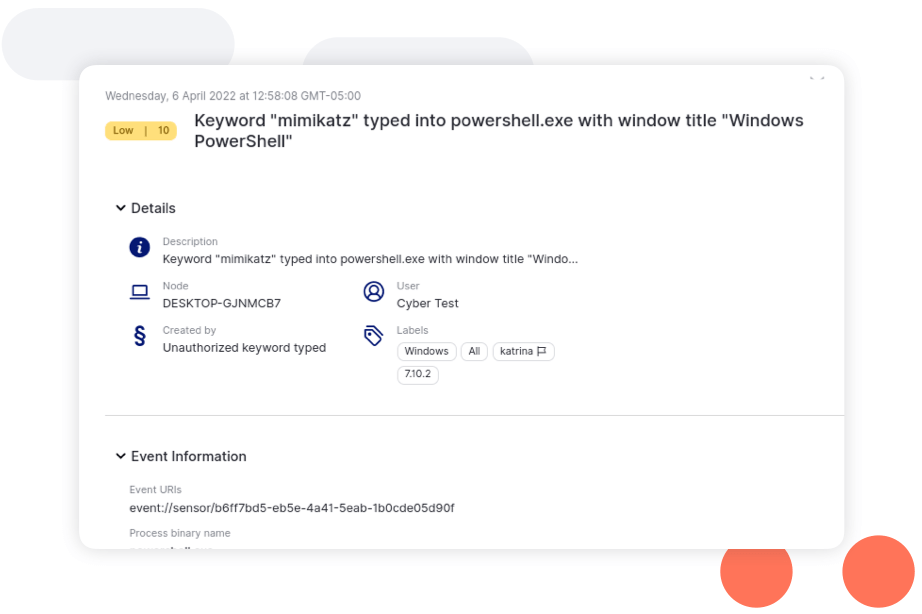
Organization-owned computers are increasingly used for both work and personal use. Using advanced mechanisms such as keystroke analytics, Reveal can detect when computers are shared with others, and even spot credential sharing.
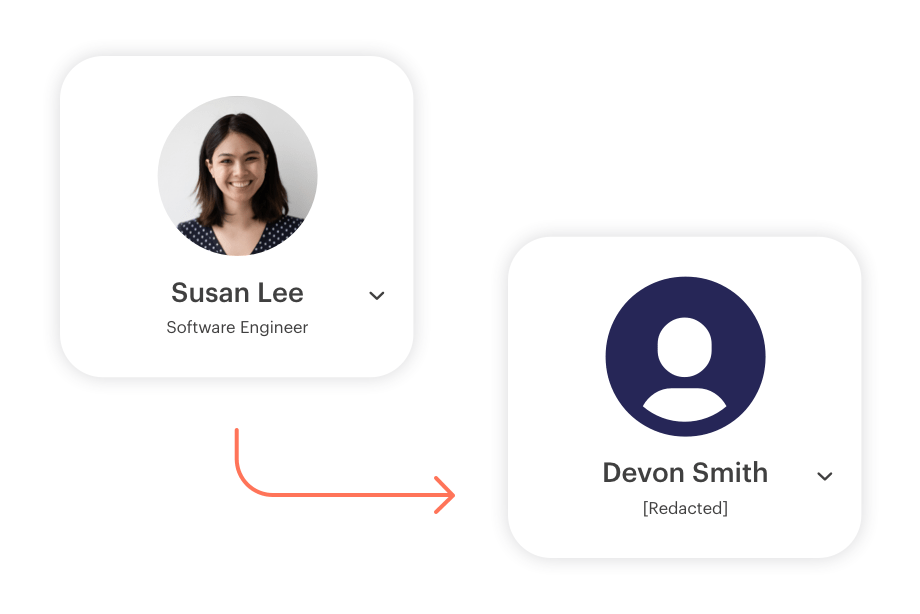
With Next DLP's industry-leading solution of pre-built data minimization techniques, such as pseudonymization and anonymization (partial and full redaction), you can now detect and mitigate threats while maintaining the confidentiality of users.
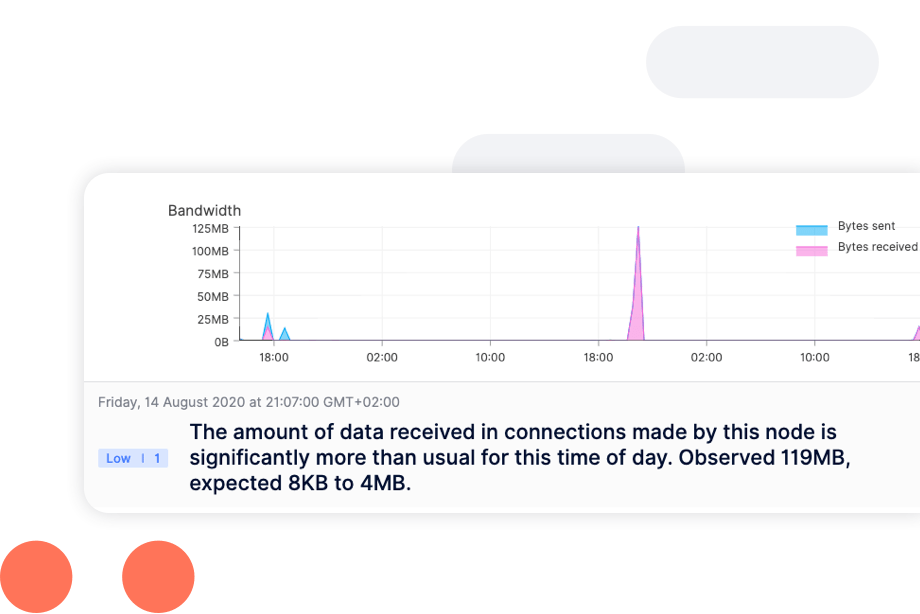
Combining these two powerful methods of detection, regardless of an employee being offline or remote. This combination analyzes more user scenarios and detects more incidents–resulting in faster threat remediation.
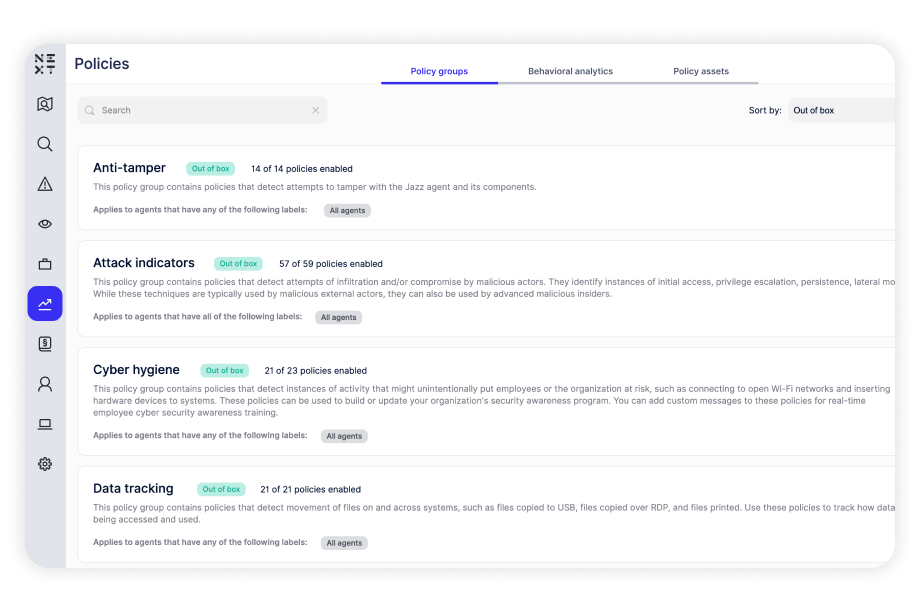
Built-in policies for data tracking, cyber hygiene, and malicious activity that can detect and defend against various risks. Policies run against computers and users, providing insight into how users access files, applications, and systems, which determine specific areas of risk.

The Reveal agent is deployed to Windows, macOS, and Linux computers and servers, where it collects granular behavioral information for security threat analysis.
Read our comprehensive post: What is User Entity and Behavior Analytics (UEBA)?
