Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

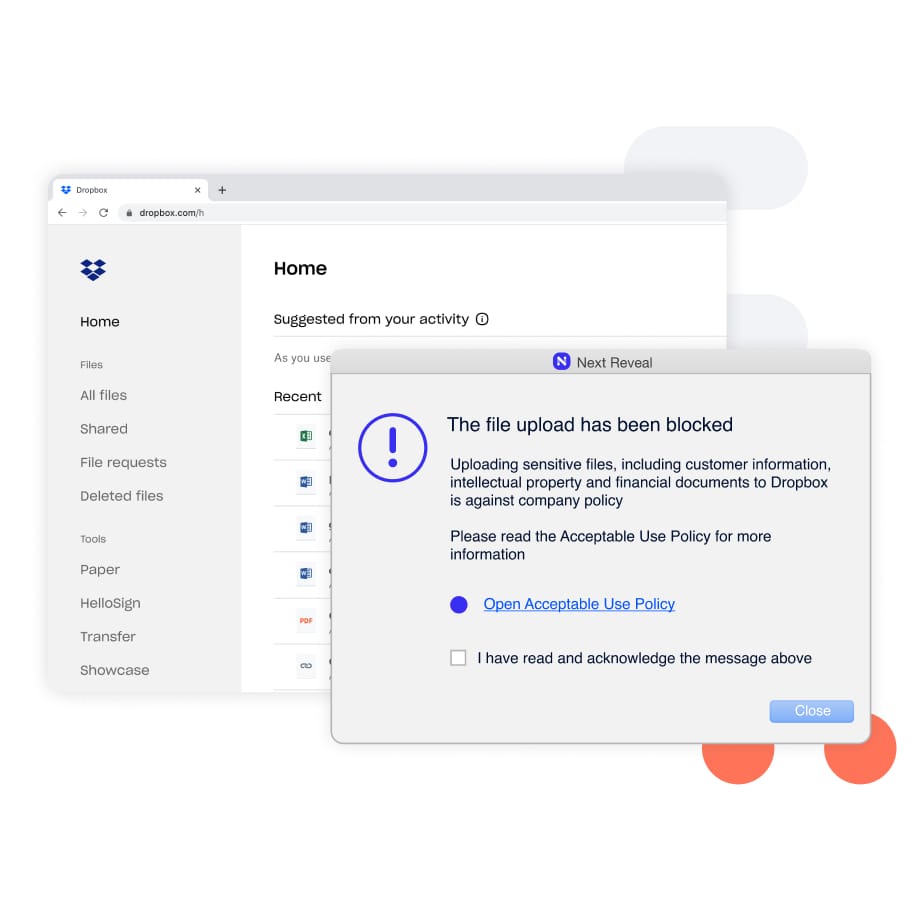
Prevent users from mounting unauthorized USB drives. Receive alerts when new devices are discovered, including CDs, DVDs, SD Cards, cameras, printers, wireless, and gaming devices.
Stop Data Loss
Real time content inspection and classification on the endpoint blocks unauthorized users from moving sensitive data such as PCI, PHI, PII, or intellectual property to USB-enabled devices while allowing transfer of files locally.