Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

How are you ensuring your OT systems are protected from attacks that could cause downtime? What prevents unauthorized applications from being installed putting your business at risk? How do you reinforce accepted use on these critical devices?
Operational Technology includes a broad range of computers, programmable systems, and other devices that interact with the physical environment. These devices run our factories, transportation systems, and other critical infrastructure. When an attacker gains control of these assets, they can injure people, damage equipment, disrupt operations, and steal sensitive information.

Protect critical systems
Real time monitoring of network and entity activity, including source/destination IP addresses, port activity, and the volume of requests to identify anomalous activity.
Identify and Block Unsanctioned Applications
Ensure that only the required and approved software is installed on OT devices.
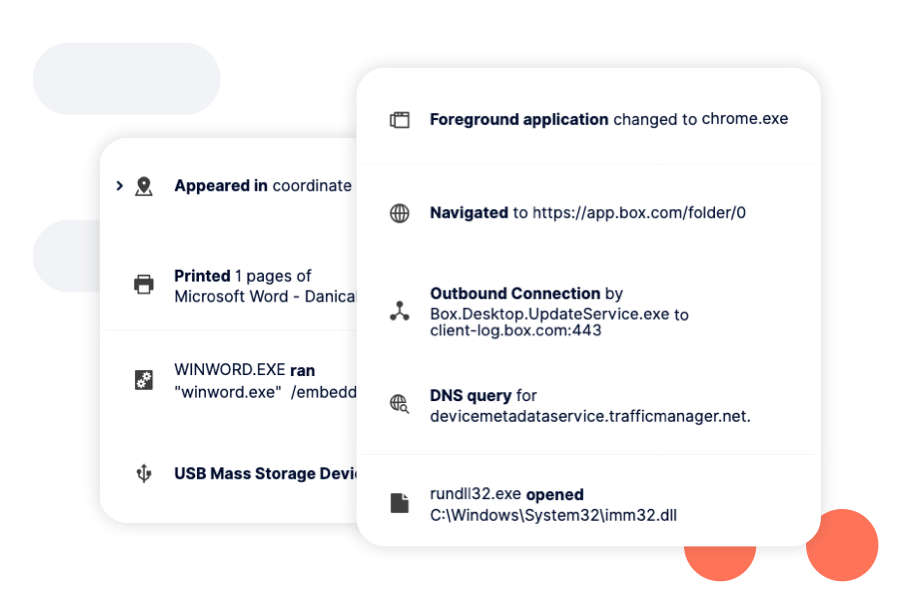
Machine learning on the endpoint identifies anomalous activity such as rapid, high volume encryption attempts and takes proactive quarantining measures such as isolating workstations to reduce the impact and spread of ransomware infections.
Educate Users
Significantly reduce your attack surface to such attacks by alerting users of suspicious links in email, use of their credentials outside of normal patterns, and USB activity.