Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
Companies know that good cyber hygiene comes from great user awareness. But busy employees don’t always have the time to keep up with cyber security education, even if mandated in company policy. With more than 90% of cybersecurity attacks targeting people, according to data analyzed from the Information Commissioner’s Office, this is a risk that organizations cannot afford to ignore.
Out of the box policies
Reveal provides a set of out-of-the-box policies that rely on granular data and smart inspection patterns. These policies provide instant protection against many insider threat scenarios that put your organization at risk – like users accessing unsafe applications, using unapproved hardware, or opening unauthorized files.
Reveal also covers several exfiltration channels like email, file sharing tools, or physical storage devices. The interface provides intuitive means of selecting, managing, and modifying policies. Policies can be activated on-demand – with a single click. And they are fully customizable, allowing operators to model Ava Reveal’s proactive, user-centric protection along with the organization’s needs.
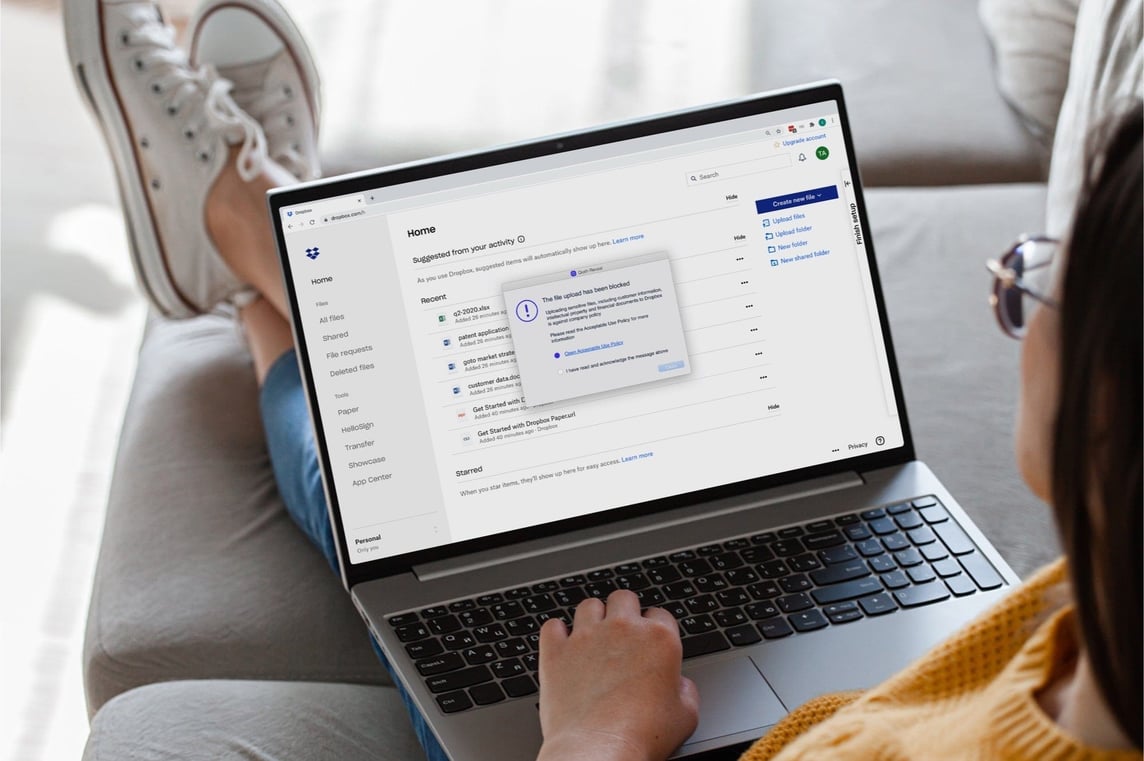
When a policy breach triggers a response action, Reveal can provide real-time feedback to educate users. It can also prevent unauthorized behavior and block threats, if necessary.
Various response actions range from displaying a popup message, redirecting the user to a sanctioned tool or application, or even providing guidance, documentation, or, most importantly, cyber security training. All of the above offer an educational opportunity to curb future events and stop those currently in progress.
Let’s run through a scenario, for example, an experienced user with high privileges. Someone with access to sensitive data like social security numbers attempts to copy this data to an unauthorized file-sharing service. The Reveal lightweight agent can detect sensitive data such as social security numbers, credit card information, and phone numbers out-of-the-box without any need for manual classification beforehand.
Reveal stops this potential data loss dead in its tracks, educating the user and redirecting them to the corporate sanctioned file-sharing service. Not only has Reveal stopped a potentially catastrophic data loss incident but has delivered cyber security awareness and education to the user, saving time and avoiding further disruption to the business.
Another example of Reveal in action could be the case of a user who may fall victim to a social engineering attack. By alerting and educating the user, Reveal augments existing security controls like endpoint detection or anti-phishing software. It warns the user of risky behaviors and delivers mandatory training via a redirect concisely and effectively. This action not only stops the attack in its tracks but reinforces education, keeping your organization and people trained and vigilant.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources