Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
The 2023 Verizon Data Breach Investigations Report (DBIR) was released this week. The annual report always makes for an interesting read. Rather than broad statistics, the report does a deep dive on the “how” and “why” of incidents and breaches. It also helps organizations understand what they can do to protect themselves by referencing the Center for Internet Security (CIS) Critical Security Controls.
First, for those new to the DBIR, some vocabulary tips. The DBIR defines an incident as “a security event that compromises the integrity, confidentiality or availability of an information asset.” A breach is an incident “that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.” For each incident or breach, the report examines the Actors (who is behind an incident or breach), Actions (how the Actor conducted the attack), Assets (the entities affected in an incident or breach), and Attributes (whether the attack affected Confidentiality, Integrity, or Availability of data).
The 2023 report covers 16,312 incidents and 5,199 total breaches that occurred between November 1, 2021, and October 31, 2022. They break down the data across 10 industries plus the mid-market. Here is what we found interesting in our first read:
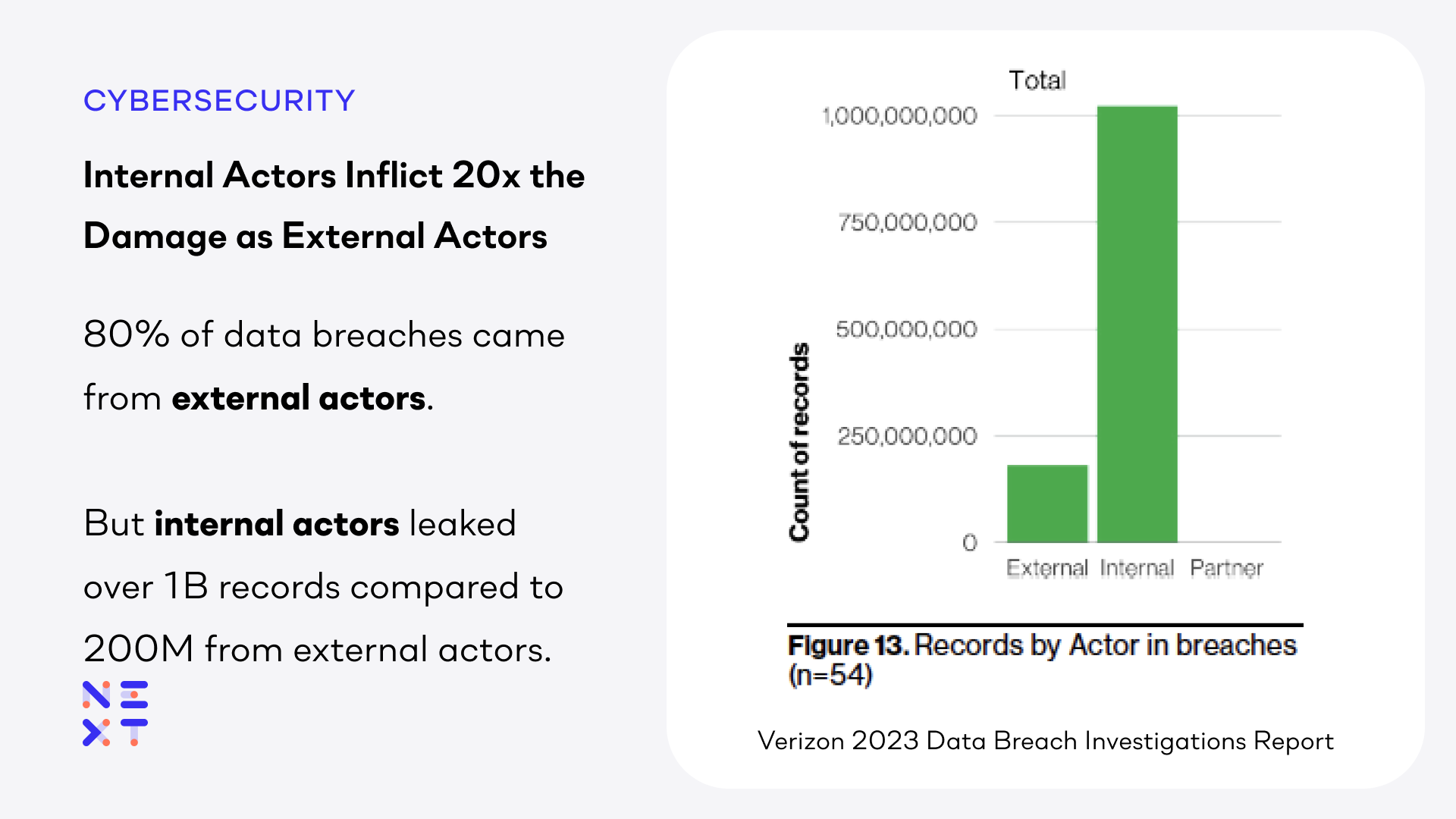
Your organization may have 100, 1,000, or 100,000 employees. These are the only “internal actors.” Everyone else in the world is an external actor. Despite those odds, insiders – employees who you trust – are responsible for 1 in 5 of the incidents they analyzed.
When we combine that with some data from the 2022 DBIR, the damage from insiders becomes more clear. While external attackers were behind around 80% of breaches in 2022, this accounted for “only” 200 million records being lost. In contrast, the 20% of breaches initiated by internal actors were responsible for losing over 1 billion records.
In other words, each internal attack exposed over 20 times as many records.
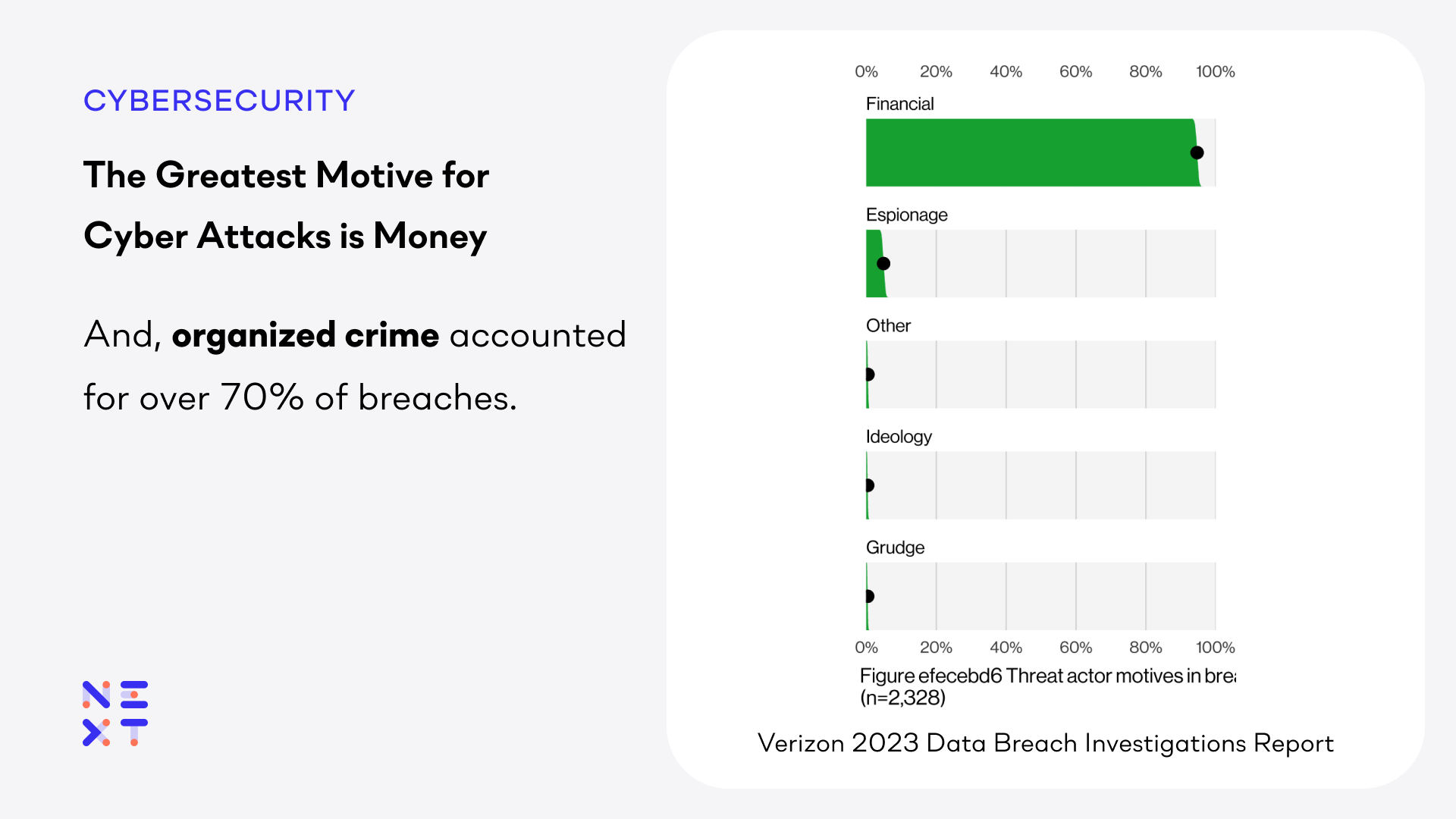
As in past years, money is still the primary motive behind attacks. Organized crime groups accounted for over 70% of the breaches. Protected Health Information (PHI) and Personally Identifiable Information (PII) can be used for identity theft and insurance fraud. Credit card information can be sold on the dark web. Your product plans can be sold to competitors.
Quite simply, your data is valuable to both you and external actors; you need to protect that data from loss or theft.
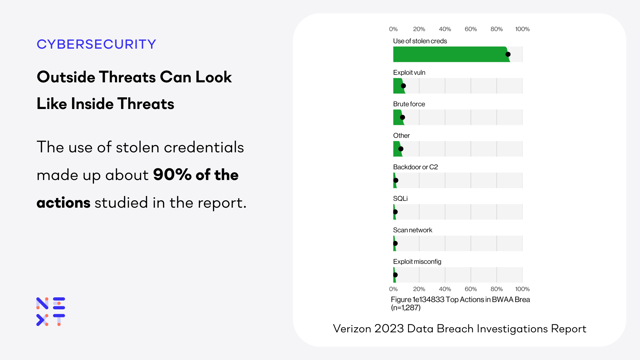
Stolen credentials are the most common attack method for breaches and credential theft is rampant. The “assume breach” paradigm acknowledges that an attacker will be able to gain a foothold in your organization. This could come from an unpatched vulnerability, a phishing attack, a malicious insider, or through the more than 24 billion stolen credentials available on the dark web. Once the attacker has legitimate credentials they can reach all the data that the user can access. Defending against this requires a solution that can quickly baseline user behavior, understand context and content to identify what data is egressing, and flag anomalous activity.
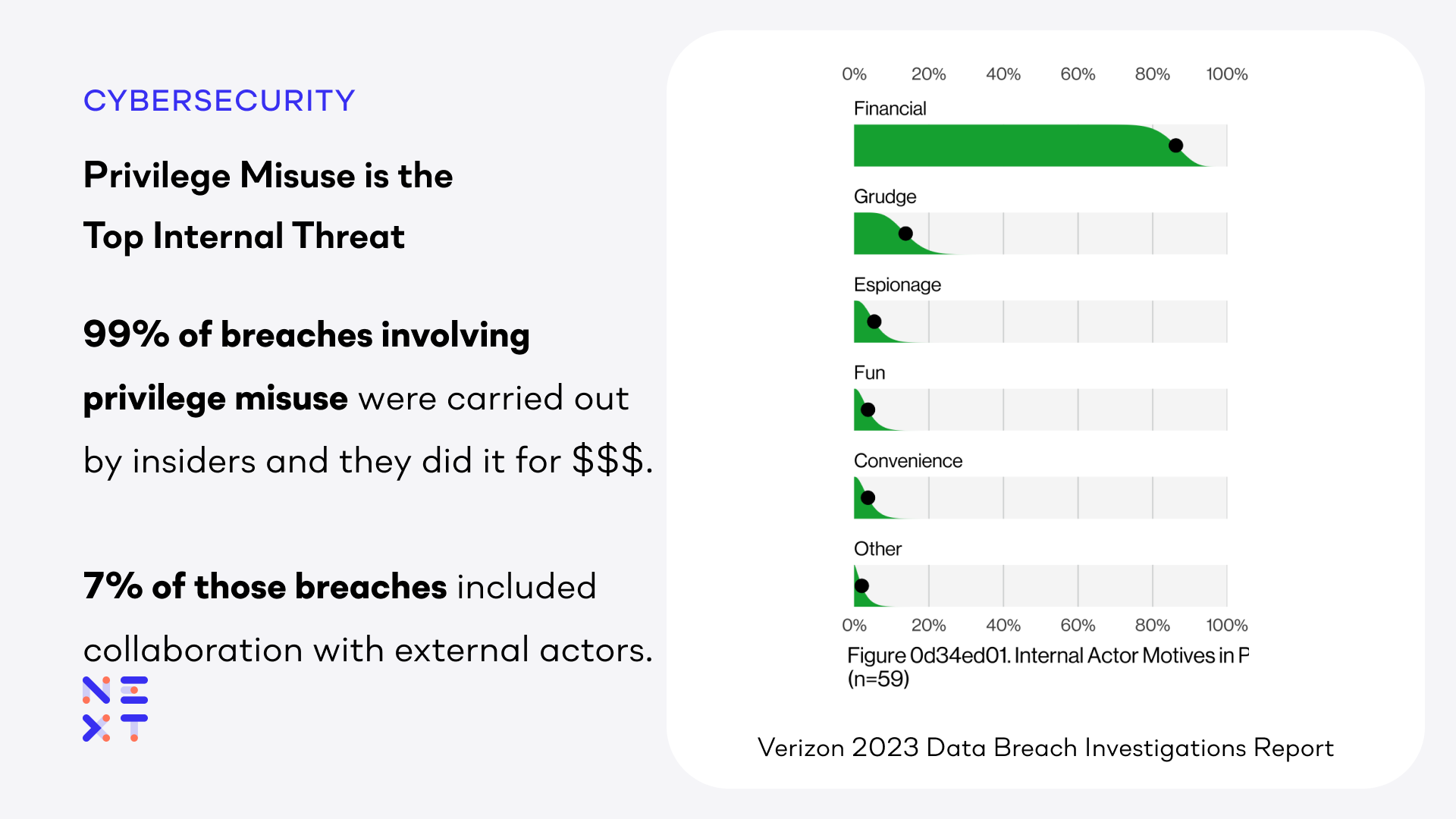
Privilege misuse is the classic insider threat scenario, using legitimate access to steal data. Not surprisingly, the threat actor is an internal user in 99% of the breaches. Interestingly, the internal actors worked with external actors (including partners) in 7% of the breaches. Verizon speculates that this indicates that the internal threats may have deliberately sought employment with the targeted organization specifically to steal data. Again, the key to combating privilege misuse is visibility to sensitive data as it is being accessed and recognizing unusual behavior.
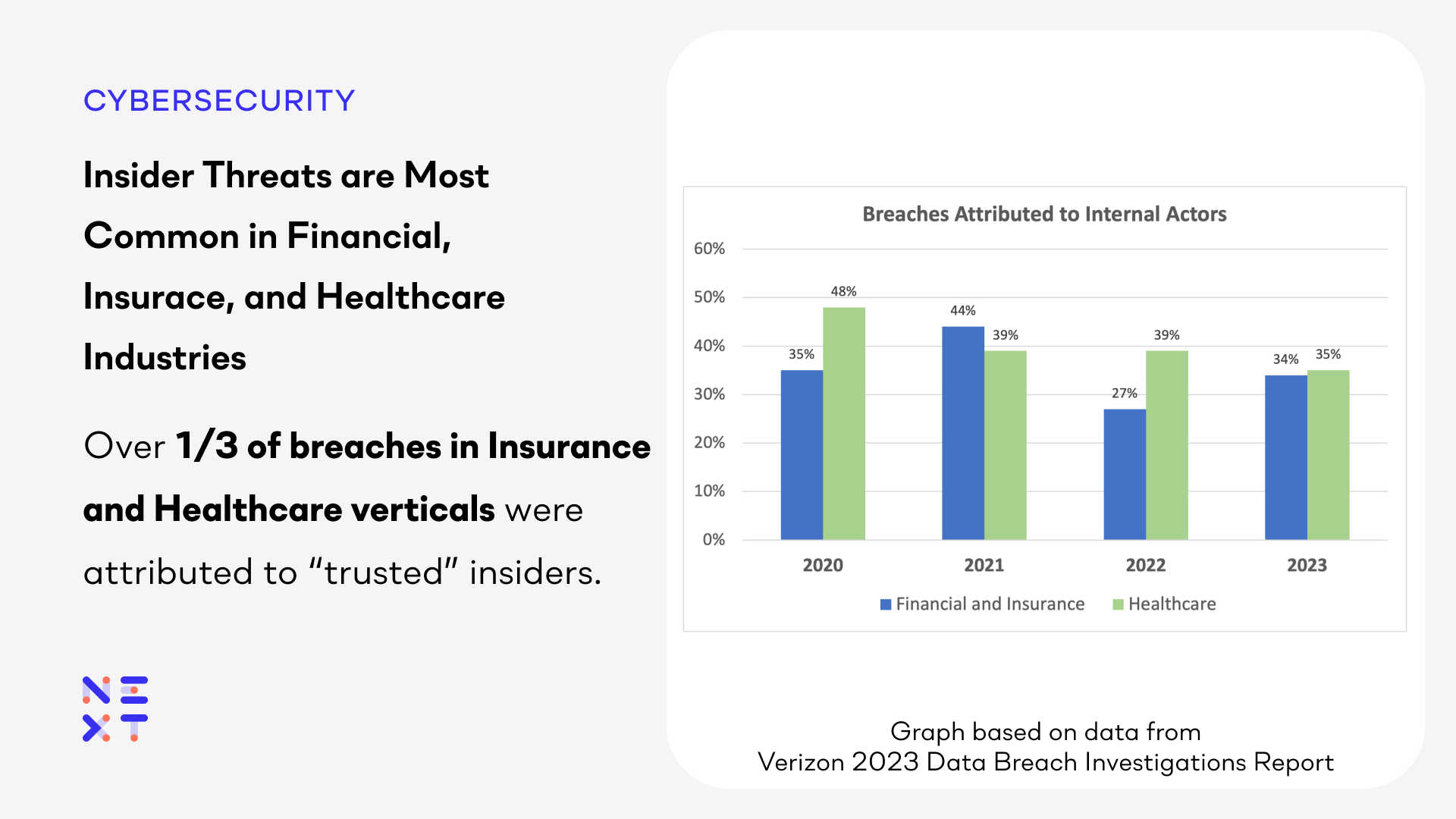
Over 33% of the breaches in the Financial & Insurance and Healthcare verticals were attributed to “trusted” insiders. This continues a trend for these markets. As shown in the graph, insiders regularly account for between a third and a half of the breaches.
It is important to understand how users access, use, and share data in any industry. The ability to identify sensitive data as it is created and used, on and off the corporate network, is critical to securing that data.
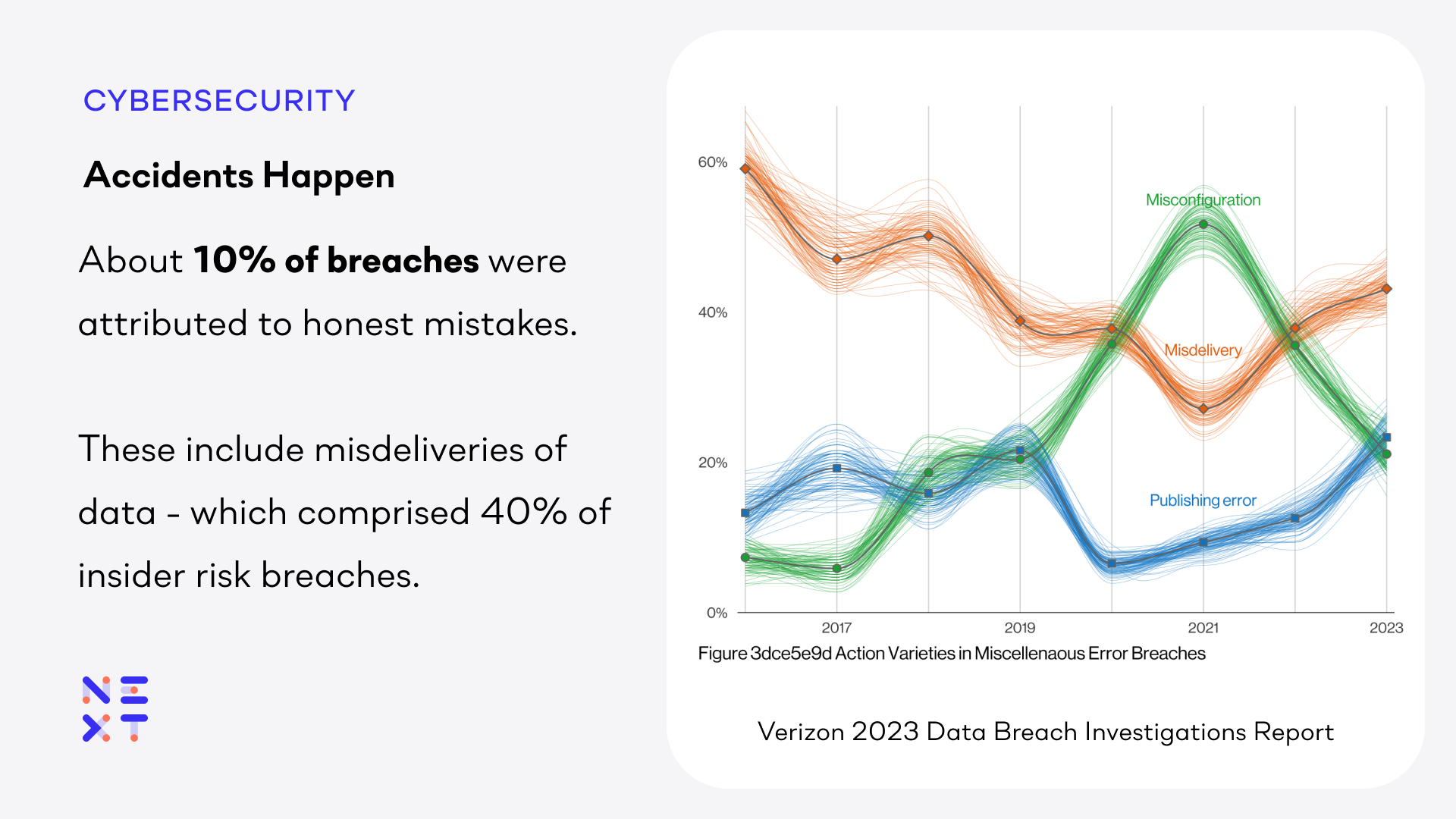
512 of the 5,199 breaches – approximately 10% – were attributable to “Miscellaneous Errors” consisting of misdelivery, misconfiguration and publishing errors. Misdelivery – sending something to the wrong recipient – accounted for over 40% of these. These are not malicious actions. Instead, they are cases where an employee simply made a mistake.
Protecting data must include accounting for the human element. Training for security awareness should be a part of any security program and is a recommended CIS control for this category. Another is to deploy a data loss prevention solution. Good solutions can recognize when a user is attempting to share sensitive data in an unauthorized manner and warn them. In the case of Reveal, it can also display company policies and require user acknowledgement.
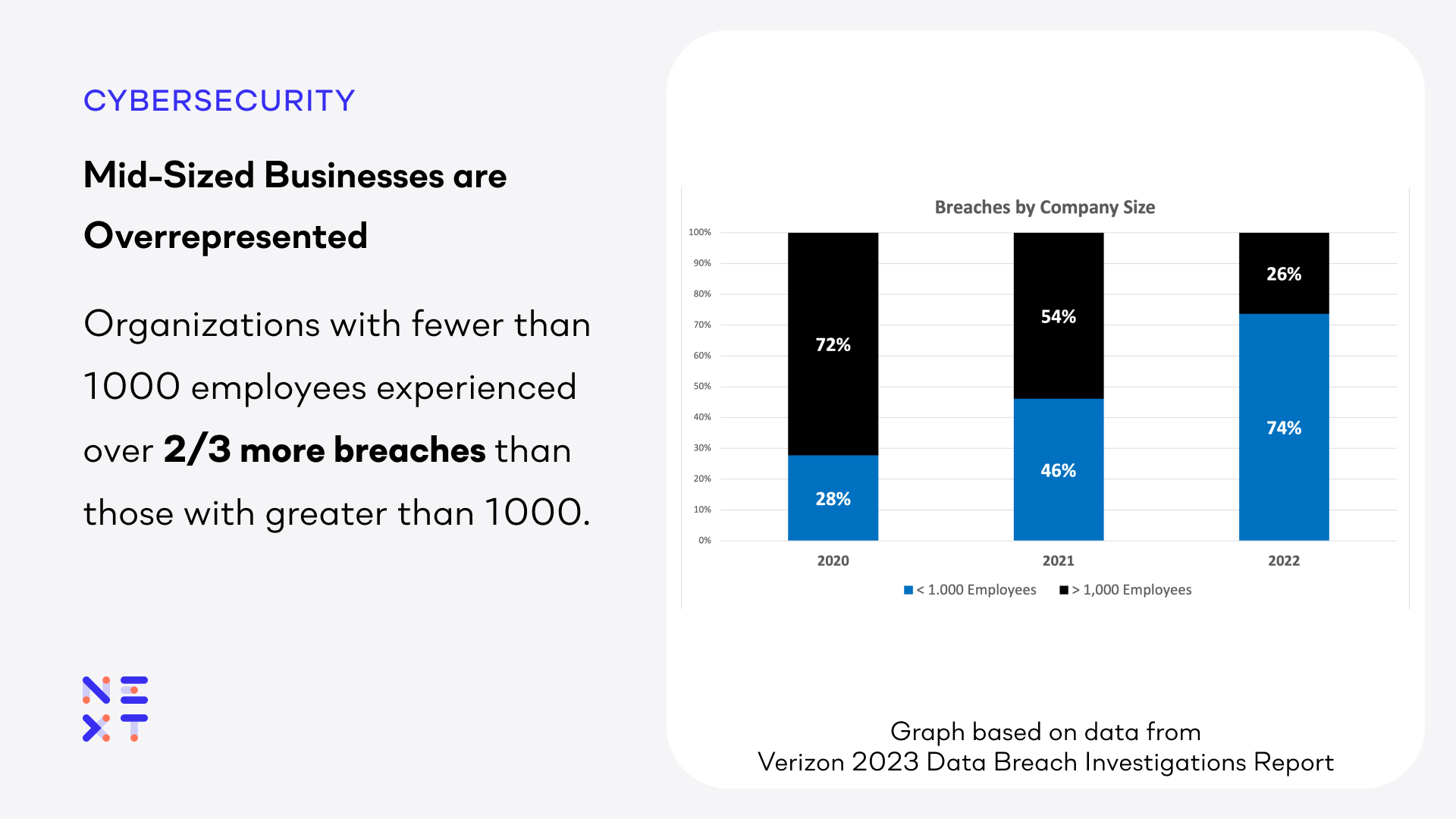
One may assume that large enterprises have more data and are therefore subject to more attacks. The 2023 DBIR finds the opposite. Organizations with fewer than 1,000 employees experienced over two thirds more breaches than those with more than 1,000 employees (381 v. 227). This likely is due to mid-sized organizations being perceived as softer targets with fewer security resources. A recommended CIS Control for the mid-market is “Data Protection: Develop processes and technical controls to identify, classify, securely handle, retain, and dispose of data.”
Our data protection solution, Reveal, uncovers risk, educates employees, and fulfills security, compliance, and regulatory needs. Unlike legacy DLP, Reveal is a flexible, cloud-native, ML powered solution built for today's threat landscape.
Want proof? Book a demo and we’ll show you how Reveal can bolster your insider risk and data loss prevention program.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
