Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
Security professionals have no shortage of threats to address. Prioritizing them can be particularly challenging. This is especially true for CISOs who must establish and maintain a robust cybersecurity strategy to protect the organization's digital assets, sensitive information, and technology infrastructure from cyber threats, attacks, and data breaches.
We were intrigued by a recent blog post from Greylock on what CISOs are prioritizing in a rapidly changing world. The key quote is:
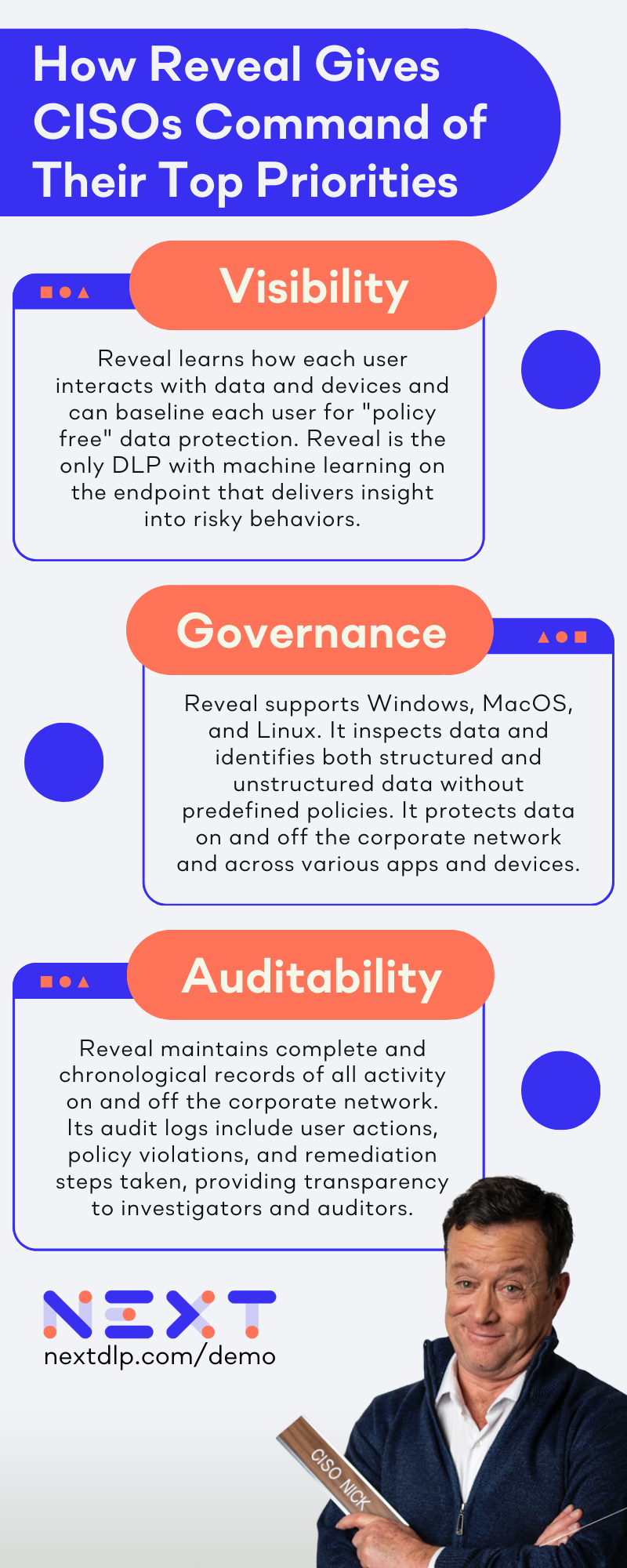
"The immediate priority CISOs face is visibility, governance, and auditability to mitigate risk.”
Let’s look at these as they apply to protecting an organization’s sensitive data.
Peter Drucker, the legendary management consultant and so-called “father of modern management”, famously said, “You can’t improve what you don’t measure.” The same is true in cybersecurity. The first step in any security initiative is identifying and assessing risk. This is true whether you are building new software, deploying new technologies such as Large Language Model AI, or protecting data from internal and external threat actors.
For data loss prevention, visibility to risk requires teams to understand who is using their sensitive data, and how. For example:
In other words, visibility to risk requires teams to understand how users work with data and which actions could put data at risk. Without this knowledge, it is impossible to apply controls that protect data while also enabling workers to have unfettered access to the information needed to support business goals.
Information governance aims to ensure that information is managed in a way that aligns with legal, regulatory, and business requirements, while also promoting accessibility, accuracy, security, and privacy. Proper information governance applies to sensitive information like personally identifiable information (PII), personal health information (PHI), trade secrets, financial data, and other intellectual property (IP). This requires organizations to ensure that data is classified appropriately based on its sensitivity, and security measures are implemented to protect data from unauthorized access, breaches, or misuse. It also requires that security measures are implemented to protect data in compliance with these regulatory standards such as data encryption.
Audit logs track who accessed specific data, when, and from where. Proper auditability is critical to a team’s ability to investigate and respond to security incidents. Auditability is also important from a compliance standpoint. Audit logs can provide evidence of the effectiveness of existing controls and required modifications. They help verify whether policies are being enforced effectively and whether users are complying with them. Deviations can be identified and addressed promptly.
 |
One of the challenges CISOs face in protecting sensitive data is outdated tools. Legacy DLP solutions were designed for a work environment where users were on corporate networks using applications that ran locally. Security analysts would code granular rules to govern data usage and perceived threats then constructed SQL queries to learn how data traveled. This took more time and effort than security teams had resources to properly support.
Reveal was designed for today’s work from anywhere, Bring Your Own Device, and Cloud application dominant environment. It leverages cloud-native infrastructure and APIs to see and control data usage without interfering with devices or legitimate data use. The Reveal console delivers simplified policy creation that doesn’t require complex coding. It meets the data protection needs of CISOs across all three priorities.
Rather than forcing organizations to identify and classify all data before protecting it, Reveal uses machine learning on the endpoint to identify and classify sensitive data as it is created, accessed, and used. Instead of spending months pre-classifying data, building granular rules, and baselining each class of users, Reveal’s begins protecting data immediately.
It can learn how each user interacts with data and devices, including normal keystroke patterns, what applications they use, and normal data usage. This allows “policy free” data protection: the system can baseline each user in a few weeks and alert on anomalous activity. Reveal is the only DLP with machine learning on the endpoint to delivers this insight in risky behaviors.
Unlike many DLP and insider risk management solutions, Reveal provides support for identifying, classifying, and protecting data across Windows, MacOS, and Linux. Content level inspection identifies patterns for PII, PHI, PCI, and other fixed data types. Contextual inspection identifies sensitive data in both structured and unstructured data without predefined policies. It protects data on and off the corporate network and across SaaS, messaging, and video conferencing apps.
Reveal plays a crucial role in addressing auditability by providing an evidentiary quality audit trail on all activity on and off the corporate network. It maintains a complete and chronological record of actions taken by individuals, systems, and processes to provide complete transparency to investigators and internal or external auditors and provide evidence that controls are in place and effective.
Reveal’s audit logs include user actions, policy violations, and remediation steps taken. In the event of a security incident, security teams can trace back the sequence of events leading to the breach, identify the point of compromise, and understand the extent of the impact.
Legacy DLP solutions often miss risky user behavior amidst the constant creation and movement of data. Reveal addresses this weakness through its event streaming capabilities. Event streaming allows organizations to stream detection, incident, and audit log events directly to SIEM for triage and correlation with information from other devices that may provide context to an alert. Once confirmed, users can use the Reveal console to block activity, lock out user sessions, kill processes, or isolate a device from the network.
To learn more about how Reveal can support your team’s security priorities, check out our on-demand demo videos.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources