Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
Today, the use of an antivirus product as the primary protective measure on endpoints is unimaginable, but that was not the case 20 years ago.
If we rewind two decades (or even as little as one in some cases), a data breach or cyber attack was typically an outside attacker infiltrating and compromising systems. This established a great deal of foundational cyber knowledge, resulting in endpoint detection mechanisms being designed to look for activities or changes on system files and processes made by an external hacker that could indicate compromise.
From the initial (and very basic) anti-virus solutions that looked for signature matches on files, to the more recent and advanced EDR solutions that looked at behavioral characteristics, the underlying theme is that they were all designed with a system-centric view of the environment.
The primary focus of EDR tools continues to be recording process and file-centric activity. If my biggest priority was visibility on registry changes made by a malicious dropper file that spawns a malicious process, an EDR tool would probably be my best bet. However, these tools can be blind to most other activity that happens on the endpoint, executed by the people who use these systems.
If studies on recent events are any indication, employee-driven data loss, unwittingly or otherwise, are becoming the leading cause of breaches. It is the users of these systems that put an organization and its data at risk.
An interesting survey of IT personnel, conducted by Opinion Matters, yielded the following opinions:
60% believe data breaches were primarily caused unintentionally by employees rushing and making mistakes
40% believe data breaches were caused by a lack of awareness
36% believe data breaches were caused by insufficient training
30% believe that internal employees leaking data to harm the organization
28% believe employees steal data for financial gain
If users are turning into the primary vector of data breaches, does this not necessitate augmenting a system-centric view of an endpoint with focus on user monitoring?
Access to a holistic view of user activity with insight into patterns and actions can enable companies to identify those that put the organization at risk of a data breach.
A tool like Reveal does not limit itself to looking at files or processes running at the endpoint. While providing in-depth visibility of those aspects, it additionally provides insight into applications accessed, bandwidth usage, browser uploads and downloads, Wi-Fi activity, location information, connection details, DNS activity, cloud share activity, and printing activity (to name a few). This can assist with preventative measures to reduce the risk of a data breach as it monitors both user and system activity prior to a data breach.
Example #1: An on-the go employee waiting at a cofee shop between client meetings
In the interest of maximizing time between meetings, this employee connects to the only available WiFi, which is insecure. The employee needs to get a couple of files to a customer and defaults to using a free file sharing site, like TinyUpload. In the rush to get work done, the employee does not think about any of the security awareness training they received when they joined the company. They do not recall the dangers of connecting to open Wi-Fi without using a VPN or the necessity in only using encrypted file sharing or approved file share. This non-malicious employee exposes company data to significant risk of compromise, and someone in the vicinity using a sniffer could easily access this data.
With user-centric activity monitoring, detection, and response
If using Reveal, warning signals would be raised one or more steps before the actual data exposure takes place.
The user would be warned about the encryption status of the Wi-Fi network and request they use VPN.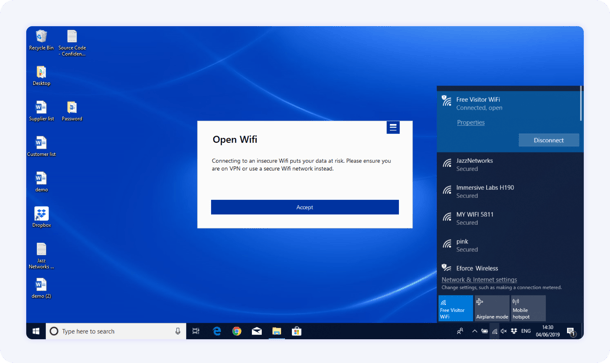
Upon connecting to TinyUpload, the user would be cautioned against using this type of file sharing.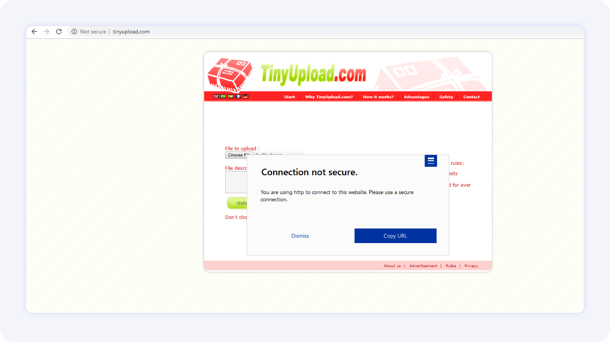
If the user still tried to upload the documents, the platform would send a warning, in this case cautioning them that doing so would put them at risk of being subject to a non-compliance fine.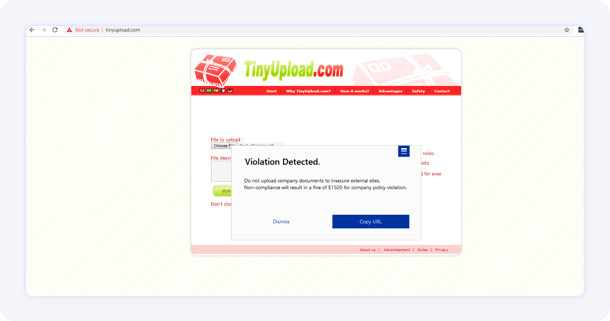
With more comprehensive visibility, detection, reinforced security awareness, and real-time policy adherence training, as shown in this example, Reveal would reduce data exposure and risk of breach to the organization.
With only a system-centric solution in place
An antivirus tool would be completely blind to this risk, and an EDR tool monitoring process and file activity would not be on the lookout for unencrypted/insecure connection activity or data transfer activity from the user. A focus on malicious system calls, registry edits or process activity is simply insufficient to raise warning signals on such activity, leaving aside the fact that reinforced user awareness or compliance training is simply not part of the DNA of those tools.
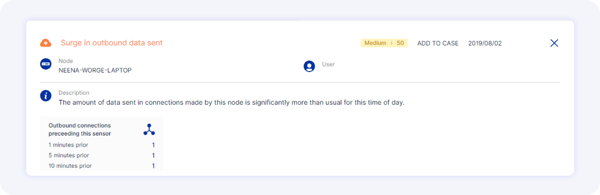
Example #2: A privileged user with compromised credentials
A hacker has gained access and uses these credentials to transfer files via a normal system tool, like PowerShell, to transfer data every night at 1 am out to an external site. Because EDR tools are typically not designed to look for bandwidth usage anomalies, these solutions would not raise any flags.
With user-centric activity monitoring, detection, and response
A user-centric behavioral analysis tool, like Reveal, that looks for normal bandwidth usage and connectivity patterns would raise warning signals.
Example #3: An employee is planning to resign and is in the final stages of interviewing with a competitor
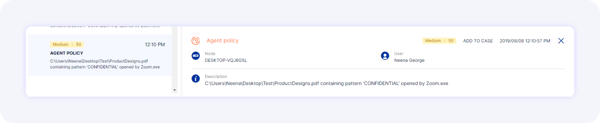
Zoom is typically used for company communication. Over a Zoom interview call with the competitor firm, the employee decides to share some proprietary company files. As a Zoom process or connection is inherently non-malicious, this activity would not be flagged by an EDR tool.
This post was originally published in Month 2020 and has been updated for comprehensiveness.
By monitoring a user’s data access and transfer, a user-centric tool, like Reveal, would catch this kind of behavior.
It is becoming more and more apparent that implementing User Activity Monitoring, or a user-centric view of your environment, is a necessary part of any cyber security strategy to fill the gaps often left by system-centric monitoring tools.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources

